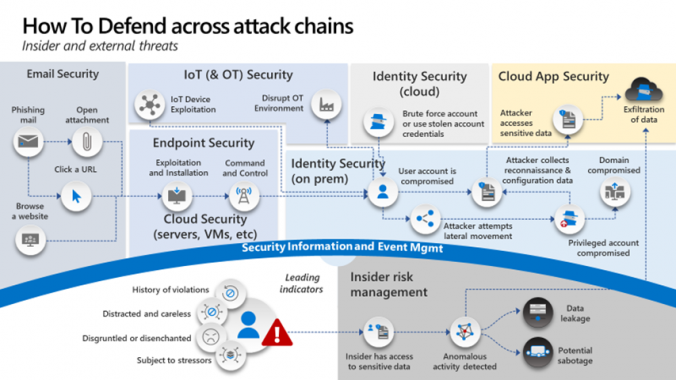
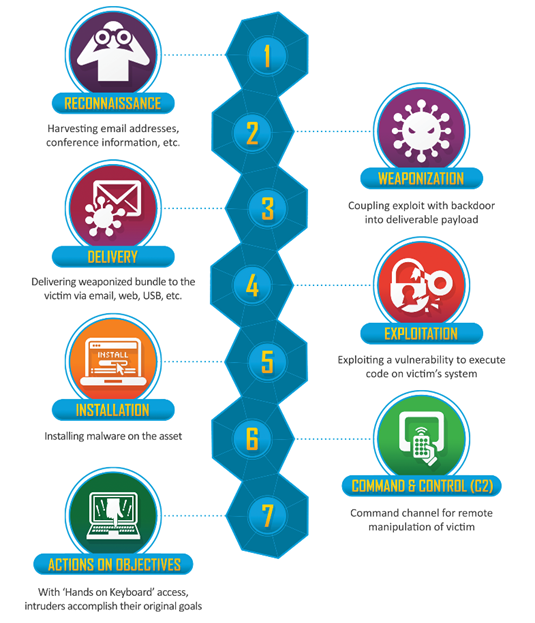
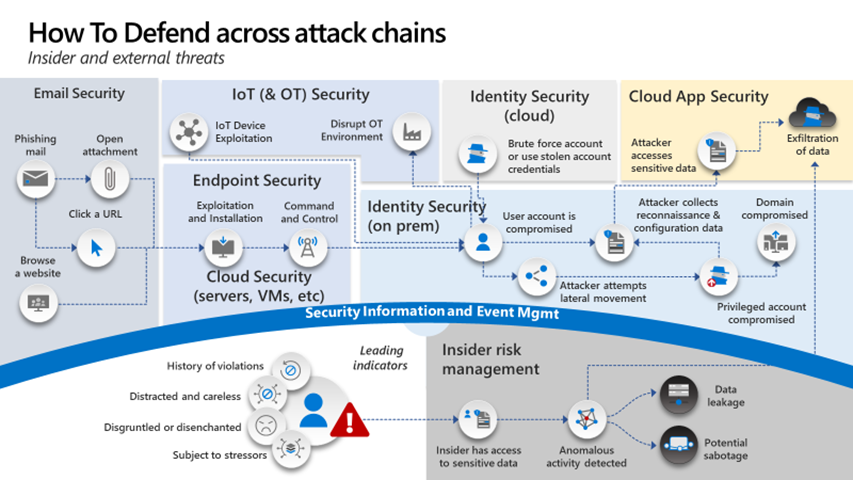
AI Security Takes Center Stage: Key Insights from DataTribe’s Cyber Innovation Day 2025 by Shawn Anderson, CTO and 2x CISO, Boston Meridian Partners
November 4th’s industry gathering revealed how artificial intelligence is fundamentally reshaping cybersecurity – from autonomous red teams to agentic AI governance
I was already a fan of DataTribe, but their daylong event at The Capital Turnaround—a historic Navy Yard car barn turned vibrant event venue—solidified my admiration. With engaging speakers, impressive startups, dynamic attendees, and great food, the event was a standout. Located in a revitalized area near the Washington Navy Yard, this venue is a must-see for your next event.
DataTribe’s Cyber Innovation Day 2025 brought together cybersecurity’s brightest minds to tackle the most pressing question facing our industry: How do we secure systems that are increasingly powered by artificial intelligence? From startup pitches to expert panels, the day revealed both unprecedented opportunities and sobering challenges ahead.
The AI Revolution in Security: Faster, Smarter, More Dangerous
The opening presentations from DataTribe’s portfolio finalists painted a picture of AI’s transformative impact. Anit Saeb, founder of Cytadel and former head of penetration testing at the Bank of England, demonstrated how AI-driven autonomous red teaming can achieve “full compromise in under 8 minutes—550x faster than ransomware groups.” According to Cytadel’s internal testing, his company’s AI agents have already bypassed the top three EDR vendors, proving that traditional defenses are struggling to keep pace.
Meanwhile, Tim Schultz from Starseer (formerly Verizon’s AI Red Team lead) highlighted a critical gap: “Current AI security tools only monitor user-LLM interactions, while agents act across databases and applications and communicate with other agents.” As organizations deploy AI agents that can independently access systems and make decisions, we’re entering uncharted territory for security governance.
The scale of this challenge became clear through Evercoast’s presentation on physical AI training. Their platform addresses a fundamental problem: “Physical AI has only thousands of hours of training data vs trillions for LLMs.” As AI systems move from chatbots to controlling physical infrastructure—from F-16 repairs to autonomous vehicles—the security implications multiply exponentially.
Industry Veterans Sound the Alarm
Jason Clinton, Deputy CISO at Anthropic, provided a sobering insider perspective on AI’s current trajectory. “AI compute [is] increasing 4x year-over-year since 1957,” he noted, with Anthropic now writing “~90% of code via Claude.” But this acceleration comes with risks: “Threat actor capability compression [is] occurring—Tier 1 and Tier 2 actors are converging as script kiddies can now ask models to write ransomware and C2 infrastructure.”
The shift in workflow is fundamental. As Clinton described it, we’re moving to “ask AI to do work, return to check results”—a complete reversal of traditional development processes. This creates new categories of vulnerabilities that traditional security tools weren’t designed to handle.
Dmitri Alperovitch, co-founder of CrowdStrike, brought historical perspective to these challenges. Reflecting on CrowdStrike’s founding after the 2010 Operation Aurora attacks, he emphasized that “if you can stop sophisticated actors, everything else becomes easy.” His advice for today’s founders was characteristically direct: “Don’t fear big company competition – fear unknown hungry startups.”
The Investment Landscape: Opportunity Amid Uncertainty
The investment panel featuring Rob Ackerman, Andrew McClure, and Phil Venables revealed a market in transition. “2025 cybersecurity financing: ~1,000 events, $15B volume with 50% being AI/AI-first companies,” they reported, but warned that “Series A to B graduation [is] declining (400 A rounds vs 40 B rounds = 10:1 ratio).”
The key insight? We’re moving from “orchestration” to what they termed “choreography” – AI agents organizing themselves in ways that traditional human-managed systems never could. This shift requires entirely new approaches to security architecture and governance.
Security Leaders Grapple with the “Lethal Trifecta”
Security practitioners Maurice Boissiere, Randy Sabett, and Pat Moynahan introduced a crucial framework for AI security risk assessment. They identified the “Lethal Trifecta for AI Agents: external data sources, external communications, and private data via unprompted input.” This framework provides a practical lens for evaluating AI deployments, though they admitted the overall assessment remains “chaotic due to AI adoption pressure vs security fundamentals.”
The panel emphasized that while “C-suite [is] now paying attention,” many organizations still lack basic incident response capabilities, with insufficient logging and “no forensic capabilities to determine breach scope.”
Media and Market Reality Check
Daniel Whitenack from the Practical AI Podcast provided valuable context on AI’s evolution, identifying three distinct phases: traditional ML (still widely used for specific tasks), foundation models (requiring technical expertise), and current generative AI that’s “squeezing out the middle” by enabling “business domain experts [to] bypass data scientists.”
Maria Varmazis from T-Minus Space Daily highlighted sector-specific vulnerabilities, noting that the “$614B global space industry” remains “10-15 years behind cybersecurity best practices.” Recent incidents include University of Maryland researchers using an “$800 antenna to intercept sensitive military/police communications” and “Russia’s 2022 ViaSat attack [that] disabled Eastern European satellite communications.”
Startup Innovation: Hardware Meets AI
Beyond software solutions, Tensor Machines demonstrated how AI security extends to physical systems. With “$2M NSF funding and 5 patents filed,” they’re addressing the “$5T+ autonomous systems market” through “physics-informed neural networks for real-time physical fingerprinting.” Their live demonstration showed automatic failover when camera spoofing was detected – exactly the kind of autonomous response needed as AI systems become more prevalent in critical infrastructure.
Lessons from the Trenches: Fundraising and Building
Throughout the day, practical wisdom emerged from battle-tested entrepreneurs. Alperovitch’s fundraising philosophy resonated: “Would you rather have 50% of a pea or 10% of a watermelon? No one ever went bankrupt because of dilution.” His emphasis on execution over technology trends – “customers buy effectiveness, not technology trends” – provided grounding amid AI hype.
The bourbon tasting session offered its own metaphor for startup persistence, featuring Charleston Red Corn Bourbon made from a “colonial-era variety that nearly died out” until a “Clemson professor found 2 cobs in seed vault [and] regenerated the line.” Sometimes the most valuable innovations come from reviving what others have given up on.
Take Action: Preparing for the AI Security Future
The insights from DataTribe’s Innovation Day point to several immediate actions every cybersecurity leader should take:
Assess your AI exposure now. Use the “Lethal Trifecta” framework to evaluate every AI deployment in your organization. Catalog which systems have external data access, communication capabilities, and access to private data without human oversight.
Invest in behavioral detection over signatures. Traditional signature-based security is already failing against AI-generated threats. Companies like Tensor Machines are pioneering behavioral fingerprinting approaches that can adapt to new attack patterns in real-time.
Prepare for agent governance. Whether you’re deploying AI agents or defending against them, establish clear policies for agent identity management, permission structures, and audit trails. The companies that solve this challenge early will have significant competitive advantages.
Bridge the talent gap strategically. With AI democratizing both offensive and defensive capabilities, focus on hiring people who can architect secure AI systems rather than just operate traditional security tools. The future belongs to organizations that can “choreograph” rather than just orchestrate their security operations.
Plan for autonomous security. As Jason Clinton noted, we’re approaching a world where “AI writes code → AI finds bugs → AI tests vulnerabilities → AI fixes issues.” Start experimenting with AI-powered security automation in low-risk environments to build competency for this inevitable future.
The cybersecurity industry stands at an inflection point. Organizations that act on these insights now—while their competitors are still debating whether AI is hype or reality—will be the ones defining security standards for the next decade. The question isn’t whether AI will transform cybersecurity, but whether you’ll be leading or following that transformation.
I attended DataTribe’s Cyber Innovation Day 2025 and compiled insights from presentations, panels, and networking sessions throughout the event.
Please reach out to us via our webpage and LinkedIn below.
Boston Meridan LinkedIn Page <- Follow this company!
About the author
Shawn Anderson has an extensive background in cybersecurity, beginning his career while serving in the US Marine Corps. He played a significant role as one of the original agents in the cybercrime unit of the Naval Criminal Investigative Service.
Throughout his career, Mr. Anderson has held various positions, including Security Analyst, Systems Engineer, Director of Security, Security Advisor, and twice as a Chief Information Security Officer (CISO). His CISO roles involved leading security initiatives for a large defense contractor’s intelligence business and an energy company specializing in transporting environmentally friendly materials.
Beyond his professional achievements, he is also recognized for his expertise in the field of cybersecurity. He is a sought-after speaker, writer, and industry expert, providing valuable insights to both C-Suite executives and boards of directors.
Currently, Mr. Anderson serves as the Chief Technology Officer (CTO) for Boston Meridian Partners. In this role, he evaluates emerging technologies, collaborates with major security providers to devise cybersecurity strategies, and delivers technological insights to the private equity and venture capital community.
Overall, Shawn Anderson’s career journey showcases a wealth of experience in cybersecurity and leadership roles, making him a respected and influential figure in the industry.