The attack lifecycle, also known as the cyber-attack lifecycle or the cyber kill chain, are the steps used to describe the various stages of a typical cyber-attack. It was an overview of the process and documented by Lockheed Martin some years ago[1]. Understanding the attack lifecycle can help organizations develop more effective cybersecurity strategies, by identifying vulnerabilities and implementing controls to prevent or mitigate attacks at each stage of the lifecycle.
In order to mitigate the threats, think of your organization as a blueprint where you have to overlay the electrical, the plumbing, the HVAC, and the network cables so you see each system individually or all at once. In this case we want to look at the data in your organization as it sits, traverses, and moves in and out of your purview of control. This view is what I call a data view and all the systems/devices working to handle this data.
You have numerous pieces of software working side by side to help with collaboration, data storage, identity management, endpoint, servers for processing, and a whole lot more. There is telemetry coming from all of this and the adversaries as well as your own internal teams can use this data for both good and bad. It is up to you, as security professionals to know the attack lifecycle and the cyber kill chain so you can implement solutions to protect your home, office, organization from exposure and exploitation.
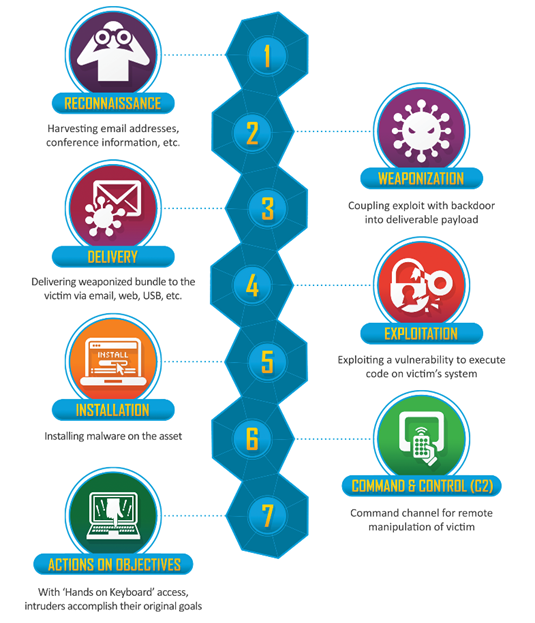
The exact stages of the attack lifecycle may vary depending on the specific model used, but generally include the following:
Reconnaissance: In this stage, the attacker gathers information about the target system or network, such as IP addresses, domain names, email addresses, and employee names. To use simpler terms this is where the adversary sits outside your house to monitor ways in, your routines, who has access, etc.
Weaponization: Here, the attacker selects the tools and techniques they will use to exploit vulnerabilities in the target system or network. This may involve creating or modifying malware or other malicious software.
Delivery: The attacker delivers the weaponized malware to the target system or network. This may be done through email phishing, social engineering, or exploiting vulnerabilities in software.
Exploitation: In this stage, the attacker uses the weaponized malware to gain access to the target system or network. This may involve exploiting known or unknown vulnerabilities in software or hardware.
Installation: Once the attacker has gained access to the target system or network, they install malware or other malicious software, which allows them to maintain persistence and control over the system.
Command and Control: The attacker establishes a command and control (C2) channel, which allows them to communicate with the malware or other malicious software installed on the target system or network.
Actions on Objectives: The final stage of the attack lifecycle involves the attacker taking actions to achieve their objectives. This may involve stealing data, altering, or destroying data, or disrupting the target system or network in some other way.
Once you understand the attack lifecycle it is my recommendation that you use some form of data analysis to track where your data is at all times. Place all the security tools your organization has on top of the cyber kill chain. Examples would be Crowdstrike or Microsoft Defender on the endpoint or using Okta, Ping, or AAD for identity. By doing this you will start to see where you have gaps or overlap.
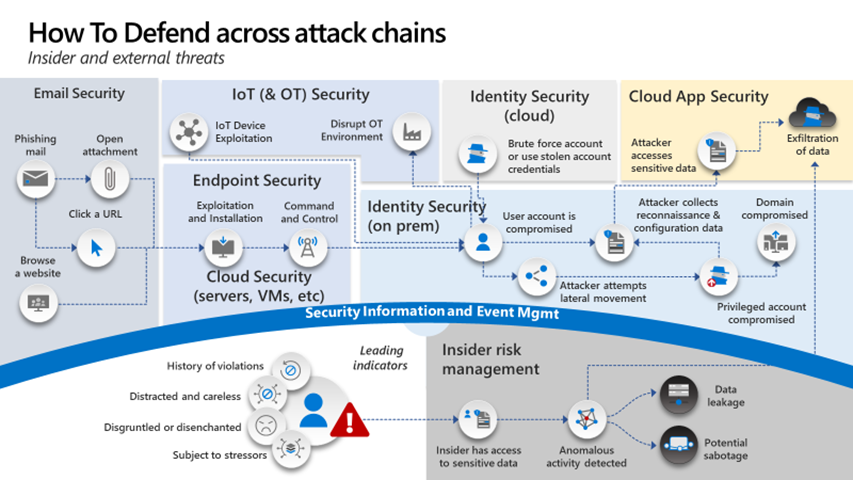
Architecting in the cloud requires a renewed focus on data and the protection of the data. Whereas networking on premises can be accomplished by putting all your data on a standalone computer and locking it in a closet. Not very productive but somewhat secure. In the cloud your attack lifecycle can be stretched because your data can be anywhere. You must build a secure architecture to accomplish this.
So, you have an assignment to review the steps an adversary would use as outlined above then take your current security tools/capabilities and overlay them on the “attack lifecycle”. Do not try and boil the ocean as this is an initial exercise to gain a better understanding of your companies’ security posture. For more detailed analysis and effort I would recommend you look at the Mitre Att&ck Framework[2]. The Mitre Att&ck Framework is not the same thing as the LMCO Attack Lifecycle. One is higher level, whereas the Mitre framework will allow you to go into techniques and sub-techniques one should protect against. There are other frameworks out there such as the Center for Internet Security Benchmark[3] (CIS Benchmark; formerly the SANS top 20) and then overlay your security capabilities over the top. It’s not an end all be all answer but will start to show you overlap, gaps, and provide a good start to now develop a plan to improve.
Take the time to study what the adversaries are doing, understand and document your organizations network, understanding where the important data is, PICK A FRAMEWORK (cannot stress this enough), and start working to put security capabilities in place to mitigate risk at every stage of the framework your organization has chosen. You will still have to assume compromise, but you will be in a much better position knowing where your gaps/risks are regarding access and protecting your data.
About the author
Shawn Anderson has an extensive background in cybersecurity, beginning his career while serving in the US Marine Corps. He played a significant role as one of the original agents in the cybercrime unit of the Naval Criminal Investigative Service.
Throughout his career, Anderson has held various positions, including Security Analyst, Systems Engineer, Director of Security, Security Advisor, and twice as a Chief Information Security Officer (CISO). His CISO roles involved leading security initiatives for a large defense contractor’s intelligence business and an energy company specializing in transporting environmentally friendly materials.
Beyond his professional achievements, Anderson is recognized for his expertise in the field of cybersecurity. He is a sought-after speaker, writer, and industry expert, providing valuable insights to both C-Suite executives and boards of directors.
Currently, Anderson serves as the Chief Technology Officer (CTO) for Boston Meridian Partners. In this role, he evaluates emerging technologies, collaborates with major security providers to devise cybersecurity strategies, and delivers technology insights to the private equity and venture capital community.
Overall, Shawn Anderson’s career journey showcases a wealth of experience in cybersecurity and leadership roles, making him a respected and influential figure in the industry.
[1] https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
[2] https://attack.mitre.org/
[3] https://www.cisecurity.org/controls/v8_pre

Leave a Reply